How to get Protected from Ransomware
It’s a very important concern for everyone that "How to get Protected From Ransomware?" In this Post, we are going to help you in securing your computers from ransomware.

Threats become more advantageous for criminals as the value of digital assets rises (in certain circumstances, they are the most valuable assets a firm owns). The highest ransomware settlement by an insurance provider to date ($40 million) occurred in 2021, and the trend shows no signs of abating.
The main issue with these kinds of attacks is that today’s computers are so fast and interconnected that malware can take advantage of those resources to spread over the network and encrypt a large number of files before the victim can react.
Ransomware attacks can disrupt network access or operations, harm your company’s reputation among customers and employees, and inspire more attacks since cybercriminals see you as a target. Recent attacks on Colonial Pipeline and Kaseya have demonstrated that no organisation is safe. Even the most sophisticated cybersecurity infrastructures struggle to deal with the aftermath of a ransomware attack, and there is no easy fix.
What are Ransomware and its Working?
Ransomware is a form of malware that encrypts or locks the data of its victims. The attackers then demand a ransom in exchange for a one-of-a-kind key that can be used to decrypt or unlock the files. A ransomware attack, like all malware, begins when a malicious payload enters the system, which commonly occurs via:
- A corrupt link or attachment.
- An ad that leads to a website with an exploit kit.
- A worm that exploits a system weakness.
- A drive-by download.
- An infected piece of hardware.
One of the most popular ways for hackers to infect a company is to send an email containing malicious links or files that an employee mistakenly clicks on to start an attack. These could be mass emails sent to millions of prospective victims or targeted emails delivered to a single person within a company.
The victim will be informed that their data has been encrypted by the attackers. The victim must pay quickly for access to the decryption key, which is commonly done in cryptocurrency to hide the attacker’s identity. Because cryptocurrency wallet addresses aren’t always hidden, the US Department of Justice was able to collect a portion of the ransom paid to DarkSide following the Colonial Pipeline ransomware attack.
If the ransom is not paid after a certain amount of time, usually 48 to 72 hours, the attackers have no qualms about raising the price and threatening to erase data. There is no guarantee that the attacker will supply the key after payment because organisations cannot anticipate good faith discussions.
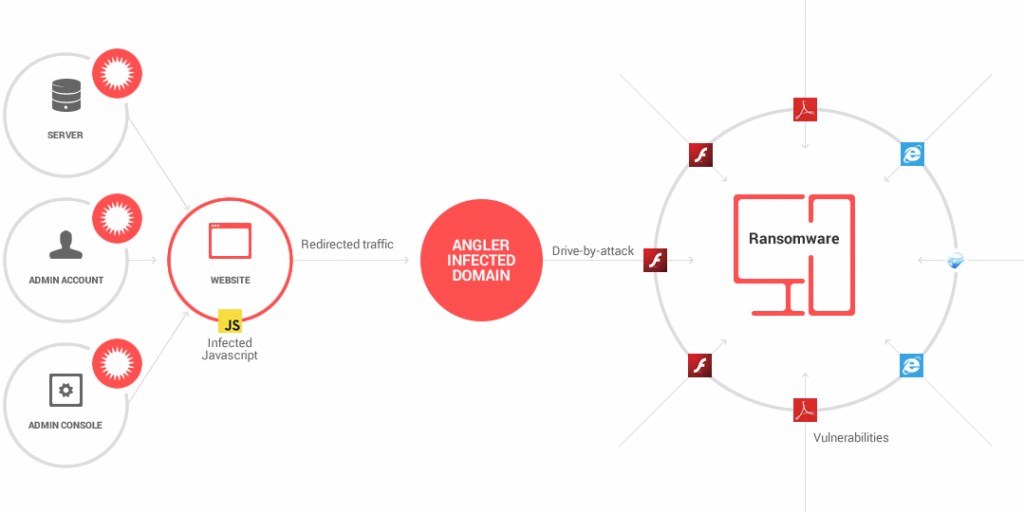
Stopping ransomware from infiltrating the network is a serious issue since it typically incorporates extraction capabilities that can steal sensitive information such as usernames and passwords. With weaknesses embedded in naïve people, stopping these attacks necessitates both staff training and a solid email and network security system that includes a strong backup programme so you can roll back to a recent copy of your data.
How To Get Protected from Ransomware?
Update Your Systems Regularly
Wanna Cry, a ransomware strain that spread around the world in May 2017, infected over 230,000 systems in less than 24 hours. The malware took advantage of a flaw in Windows’ SMB file-sharing protocol, which allowed it to travel across the network without being executed by the user.
You didn’t need to run anything to get infected; simply being on the same network as someone who did was enough, as was having an unpatched version of Windows. Only those firms who were not as vigilant with their software updates were harmed by the attack, as Microsoft had released a security fix a month prior, in April. The first line of defence is to keep your systems up to date, which can usually be automated.
- Use Immutable Backups
An immutable backup works in the same way as any other data backup, except it prevents anyone from changing or deleting data. This backup is the best defence against data corruption, whether intentional or unintentional. Back up your data at least twice a day, use at least two backups and maintain one instance offline.
If you get infected with ransomware, delete your previous system and restore the last clean backup you have. Even if you can recover the data, remember that losing confidential consumer information to criminals is still a problem. Hackers may sell or leak information, so in addition to an immutable backup, take the time to put up extra safeguards.
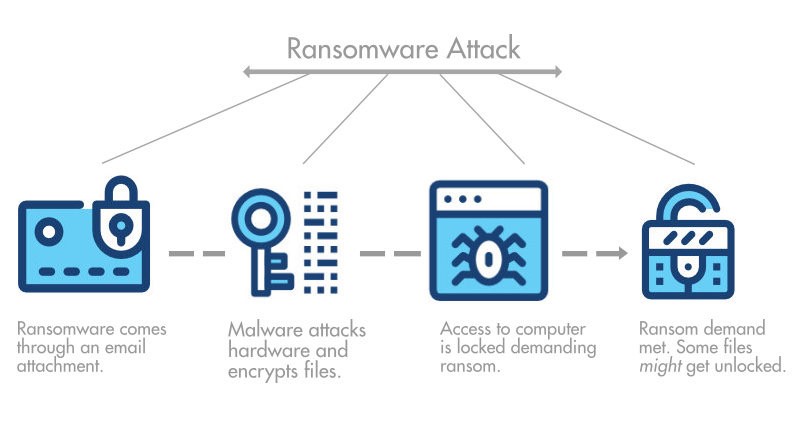
- Be Aware of Phishing Emails
In ransomware intrusions, phishing is the most common attack vector. The attacker will first deliver malware in the form of a seemingly harmless file, such as an Excel or Word document.
This virus, also known as a dropper, is in charge of downloading the primary malware that will encrypt the files and maybe other malware that would exfiltrate other valuable data found on the network, such as intellectual property, passwords, and trade secrets. Phishing is a difficult problem to overcome since individuals are focused on their work and don’t anticipate being duped.
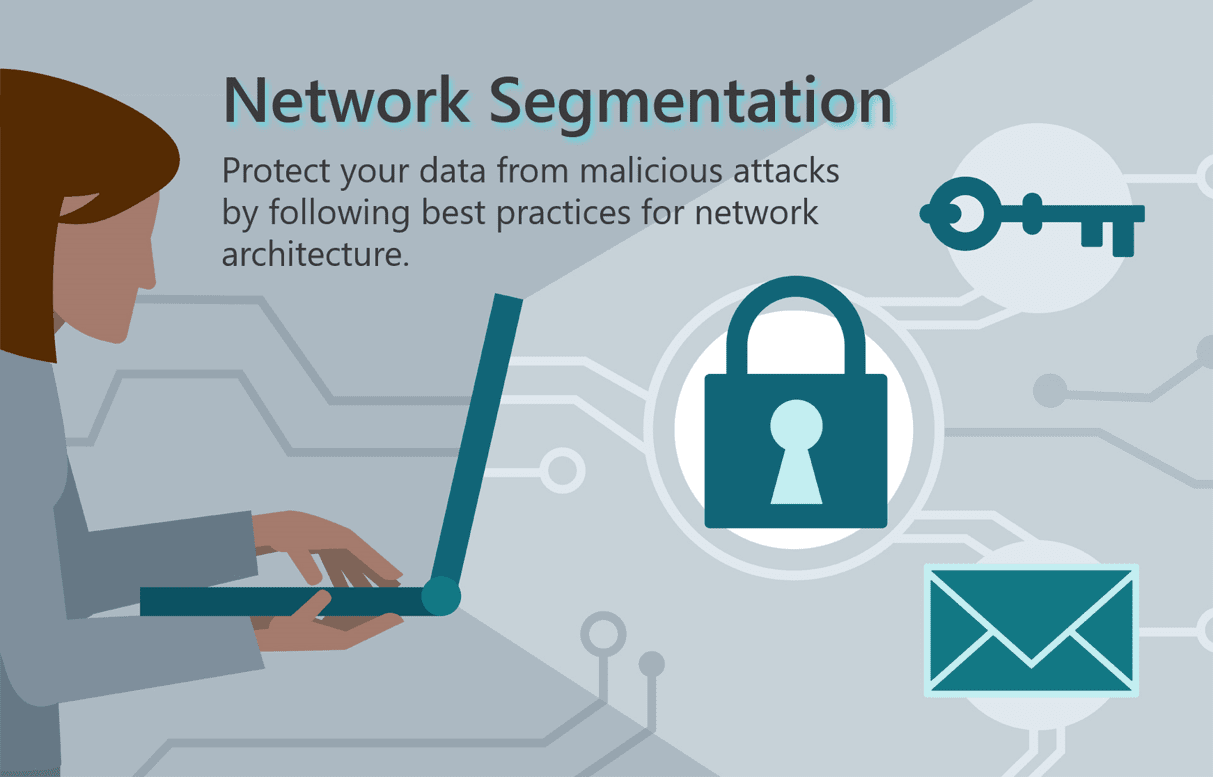
Segment Your Network.
Once ransomware has infiltrated your system, it must traverse the network in order to reach its target files. Intruders can’t move freely between systems and devices because of network segmentation. Ascertain that each network subsystem has:
- Individual security controls are available.
- Access policies that are strict and one-of-a-kind.
- A firewall and a gateway that are independent.
If intruders get access to a portion of your network, segmentation stops them from accessing sensitive information. The security team has more time to identify and isolate the threat because attackers take time to break into each component.
- Think Hard Before Paying The Ransom
If you’ve been infected with ransomware and your data has been encrypted, you might be tempted to pay the ransom. After all, paying the ransom may appear to be the less expensive alternative in the near future. However, you should consider your options carefully before making a payment. To begin with, paying the ransom does not guarantee that the attackers will decrypt your data; they could simply want more money.
Furthermore, it indicates that targeting your firm is profitable, and they (and others) will do so again in the future. Criminals may use a double extortion attack to get you to pay the ransom, in which they first exfiltrate confidential company information before encrypting the files and then threaten to reveal those secrets if the ransom isn’t paid.
- Set Up a Firewall
The first software-based line of defence against ransomware is a firewall. Firewalls monitor incoming and outgoing traffic for signals of harmful payloads, allowing the security team to keep an eye on them.
Consider putting in place the following to assist your firewall activity:
- Workloads are actively tagged.
- Hunting with a threat.
- Evaluation of traffic for mission-critical applications, data, or services on a regular basis.
Deep packet inspection (DPI) is a feature that your firewall should have in order to evaluate the data content. This feature detects malicious software in packages automatically.
- Enforce Strong Password Security
Strong passwords must be understood by your employees. Unfortunately, standard password practices leave a lot to be desired:
- Three out of four users, on average, use the same password for various applications.
- A third of Internet users use a password that is significantly weak, such as abc123 or 123456.
Remember that ransomware attacks frequently begin by taking advantage of sloppy staff behaviour. Ascertain that all employees have strong passwords that are updated on a regular basis. Otherwise, a simple brute-force attack can be used to break into your system.
Consider implementing multi-factor authentication, which requires users and workers to confirm their identities in numerous ways before gaining access to a system.
Ransomware is still one of the most profitable attacks for criminals, which means it’s also one of the most expensive for you. You have no control over attacks, thus you can’t stop them from happening. What you can do, though, is make attacking your company as costly as possible. You don’t have to outrun the bear, just the guy running next to you, as the expression goes.
Also Read: How to Perfect the Art of Twitter Marketing